Physical-layer security enhancement method for wireless HetNets via transmission pair scheduling
Ding Xiaojin Song Tiecheng Zhang Gengxin
(1Jiangsu Engineering Research Center of Communication and Network Technology, Nanjing University of Posts and Telecommunications, Nanjing 210003, China)(2National Mobile Communications Research Laboratory, Southeast University, Nanjing 210096)
Abstract:In order to enhance the physical-layer security of wireless transmission in a wireless heterogeneous network (HetNet), a two-stage-based cooperative framework is advocated. To be specific, a source-destination (SD) pair is opportunistically chosen at the beginning of the transmission slot, which can be used to assist the transmissions of other SD pairs. Under this framework, a transmit antenna selection assisted opportunistic SD pair scheduling (TAS-OSDS) scheme is proposed, and the intercept probability (IP) of the proposed TAS-OSDS, the conventional round-robin source-destination pair scheduling (RSDS) and the conventional non-cooperation (non-coop) schemes is also analyzed, where the RSDS and non-coop schemes are used for comparison with the proposed TAS-OSDS. Numerical results show that increasing the number of the SD pairs can effectively reduce the IP of the TAS-OSDS scheme, whereas the IP of the RSDS and the non-coop remain unchanged with an increasing number of the SD pairs. Furthermore, the TAS-OSDS scheme achieves a lower IP than that of the RSDS and the non-coop schemes, showing the superiority of the proposed TAS-OSDS.
Key words:wireless heterogeneous network; physical-layer security;source-destination pair scheduling
Wireless heterogeneous networks are capable of increasing the efficiency and flexibility of wireless systems, which are composed of various independent subsystems[1-2]. In a heterogeneous wireless network, various subsystems may be allowed to perform their respective wireless transmissions simultaneously. However, due to the broadcast nature of radio propagation[3], and the open system architecture of heterogeneous wireless networks[4], the confidential messages may be vulnerable to eavesdropping attacks when they are transmitted by heterogeneous wireless systems independently. Thus, the risk of confidential messages being successfully eavesdropped upon will be increased significantly. As a result, more research efforts should be devoted to protecting wireless transmissions transmitted by heterogeneous wireless networks against malicious eavesdropping.
Physical-layer security (PLS)[5-6]emerges as an effective method to guard against wiretapping with the aid of its ability to exploit the physical characteristics of wireless channels. Recently, PLS has also been designed for spectrum-sharing aided heterogeneous networks[7-8]. Jamming schemes were investigated in Ref.[9]. To be specific, in order to impose an interference on the eavesdroppers, the jammers were invoked to transmit jamming signals, whereas the amount of the interference imposed on the scheduled users was considered to be below a threshold. Single-input multiple-output (SIMO) and multiple-input multiple-output (MIMO) techniques[10-11]have been investigated to decrease the secrecy outage probability of wireless transmissions. In Ref.[12], the antenna selection was conceived to improve the PLS of wireless transmissions in the presence of an eavesdropper.
In this paper, we investigate the PLS of a heterogeneous wireless network consisting of multiple SD pairs in the presence of an eavesdropper. Differing from Refs.[7-12], the cooperation between various SD pairs has been explored to defend against malicious eavesdropping relying on a conceived cooperative framework. Moreover, we propose an SD pair scheduling scheme to improve the PLS of wireless transmissions. The main contributions of this paper can be summarized as follows. First, a heterogeneous cooperative framework is conceived to protect wireless transmissions against eavesdropping with the aid of two stages. Secondly, we propose a specific SD pair scheduling scheme, called the TAS-OSDS. In the TAS-OSDS scheme, one antenna of the chosen SD will be selected to transmit the repacked data to enhance the PLS of the transmitted data. Finally, it is shown that the IP of TAS-OSDS scheme will be beneficially reduced by increasing the number of SD transmission pairs.
1 System Model and Opportunistic SD Scheduling
1.1 System model
As shown in Fig.1, we investigate a wireless system consisting ofMsource-destination (SD) pairs in the presence of an eavesdropperE, where an source node (SN)Smhas the ability to communicate both with its corresponding destination node (DN)Dm,m∈{1,2,…,M}, and with other SNs at different transmission stages. For notational convenience, the set of SD pairs is assumed to be denoted asΦ.Ewith the aid of a wide-band receiver is deployed to wiretap the signal transmitted by the legitimate SD pairs. Moreover, we also assume that all DNs are connected with each other through the core network, and thus, each DN has the ability to forward the received data to other DNs. Furthermore, Rayleigh fading is used to characterize both the main links (spanning from the legitimate transmitters to the legitimate receivers) and the wiretap links (spanning from the legitimate transmitters to the eavesdropper).
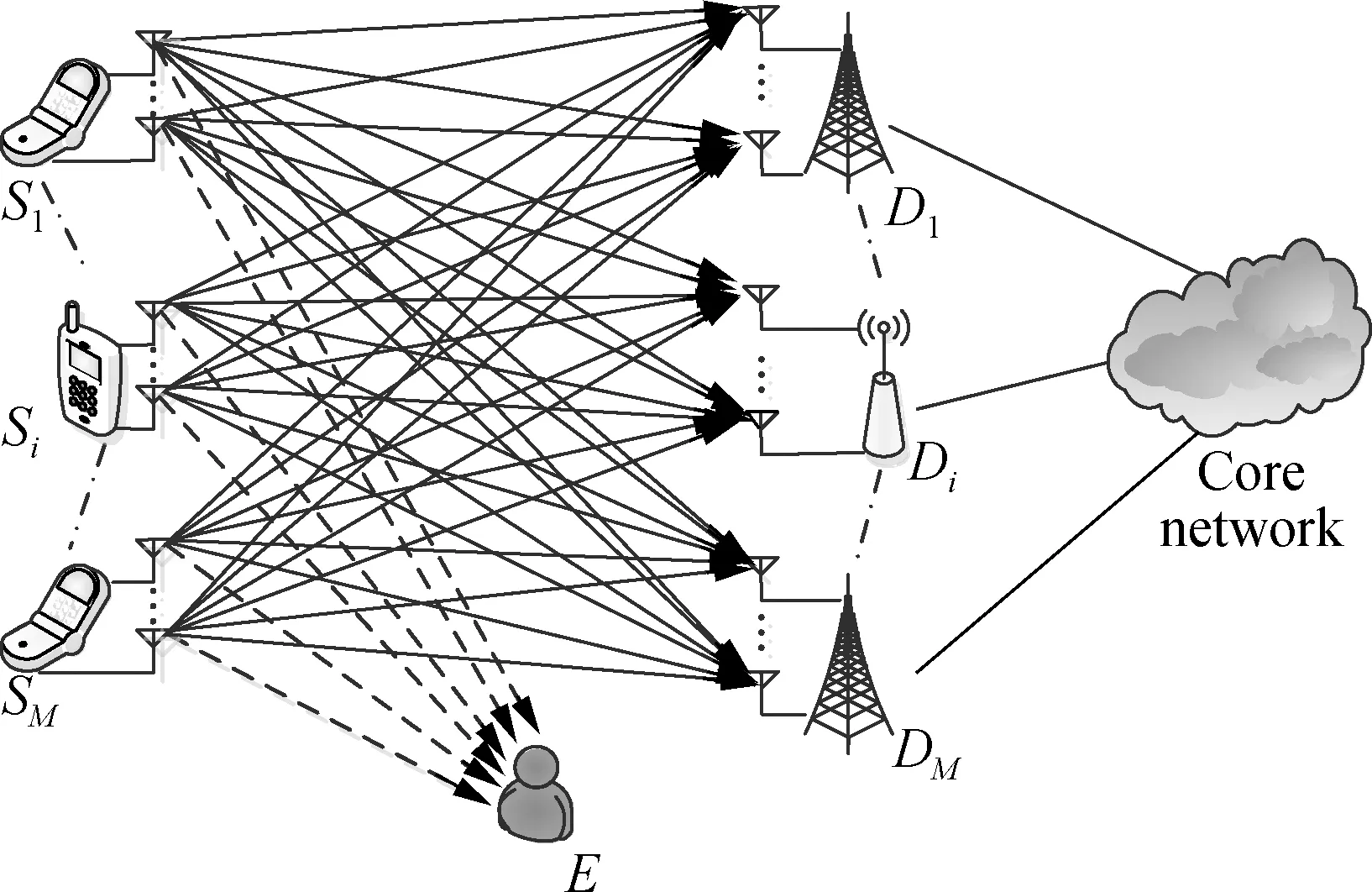
Fig.1 A heterogeneous wireless network with M multiple source-destination pairs in the presence of an eavesdropper
In order to improve the PLS of wireless transmissions of the multiple SD pairs, a heterogeneous cooperative framework is invoked with the aid of two stages. More specifically, at the beginning of the first stage, an SD pair will be chosen to be a transmitting node relying on the criterions of the RSDS and the TAS-OSDS schemes. Then, in order to help other SNs to forward their data, the chosen SD pair will receive the data of other SNs through a high-reliability low-power interface, and then repack the received data and its own data. At the second stage, the specifically selected SN may forward the repacked packet to its DN. After decoding the packet, the DN will send the sub-packets to the other DNs relying on the index of the pair in the sub-packet via the core network.
1.2 Signal model
Without loss of generality,Smis assumed to be the selected transmitting node in the first stage. As mentioned above, other SNs will transmit their signal toSm. Moreover, we also assume that only one antenna ofSkis chosen to transmit its data toSm, which is represented by antennai. Hence, the signal received atSmtransmitted bySk,k∈Φ-{m}, can be shown as
(1)
wherePs,xk,hskismjandnsmare the transmit power ofSk, the transmit signal ofSk, the instantaneous channel gain of theSki-Smjlink, and the thermal noise received atSm, respectively. Moreover,NTis the number of antennas ofSm. Meanwhile, since the broadcast nature of radio propagation,Emay also overhear the signal transmitted bySk, which can be given as
(2)
wherenerepresents the thermal noise encountered atE, andhskieldenotes the channel gain ofSki-Ellink.
From Eq.(2), and using maximal-ratio combining (MRC), we can obtain the channel capacity of theSk-Elink as
(3)
In the second stage, we also assume that one antenna ofSmis invoked for forwarding the received data toDm. Without loss of generality, we assume that the antennaiofSm,i∈{1,2,…,NT}, is chosen to transmit packetxstoDm. Hence, the signal received atDmcan be expressed as
(4)
wherehsmidmjandndmdenote the channel gain of theSmi-Dmjlink, and the thermal noise encountered atSm, respectively. Moreover,NRdenotes the number of antennas ofDm, andPtrepresents the transmit power ofSm.
Similarly to Eq.(2),Emay overhear the signal transmitted bySm, which is
(5)
wherehsmieldenotes the channel gain of theSmi-Ellink.
With the aid of Eq.(4) and MRC, the instantaneous channel capacity of theSm-Dmlink can be obtained as
Csmdm=log2(1+γsmdm)
(6)
Utilizing Eq.(5) and MRC, we can obtain the instantaneous channel capacity of theSm-Elink as
(7)
From Eq.(3) and Eq.(7), and utilizing the maximum of individual channel capacity of theSm-EandSk-Elinks in the first and second stages, we can obtain the overall capacity of the signal fromSkas
(8)
In contrast, since the signal fromSmis only transmitted at the second stage, the overall capacity of the signal ofSmcan still be given as
(9)
Noting that given the chosen transmission pair, the signal of the chosen SD will only be overheard byEonce, due to the fact that it is only transmitted at the second stage. Differing from the chosen SD, the signal of other SDs will be overheard both in the first state and in the second stage, which are represented by Eq.(2) and Eq.(5), respectively.
1.3 TAS assisted opportunistic SD scheduling scheme
In this subsection, a TAS assisted opportunistic SD scheduling (TAS-OSDS) scheme is proposed. Specifically, in order to enhance the PLS of wireless transmissions of multiple SD pairs, an SN with the maximal channel capacity in setΦwill be chosen to be as the transmitting node at the given time slot, which will help other SNs to forward their data to their DNs. Hence, relying on Eq.(6), the SD pair scheduling criterion of the TAS-OSDS scheme can be shown as
(10)
whereorepresents the index of the chosen SD pair in the TAS-OSDS scheme, andadenotes the index of the selected antenna of the chosenSo. Moreover, Eq.(10) can be rewritten as
(11)
which can be performed in a distributed manner. The processing procedure of the TAS-OSDS scheme is shown as follows:
1) Assume that the number of SD pairs isM, and each SN is required to maintainNTtimers.
2) At the beginning of the first stage, the TAS-OSDS scheme will be triggered.
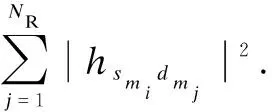
4)Sowill notify other SNs that it is the optimal node via broadcasting a notification. Then, other SNs transmit their data toSo, which will repack the received data and their own data.
5) At the second stage,Sowill forward the repacked data to its corresponding DN relying ona-th antenna ofSo. Once the transmission is finished,Dowill send other SNs’ data to their corresponding DNs relying on the core network.
2 Intercept Probability Analysis over Rayleigh Fading Channels
In this section, we analyze the intercept probability of the RSDS and TAS-OSDS schemes over Rayleigh fading channels.
2.1 Conventional RSDS scheme
As a benchmarking scheme, we present the IP analysis of the traditional RSDS scheme. With the conventional RSDS scheme, each SD pair in setΦhas the same chance to be chosen to transmit at the given time slot. Based on the definition of the IP[12], the IP of the signal fromSmandSkin the first and second stages for the RSDS scheme relying on theSm-Dmpair can be shown as
(12)
and
(13)
Combining Eqs.(6), (8) and (9), we can obtain
(14)
and
(15)


(16)
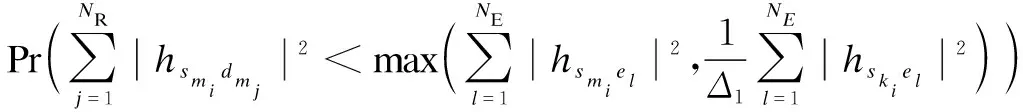
(17)
respectively, whereFU(u) is the cumulative distribution function (CDF) of RVU, andfX1(x1) andfX2(x2) are the probability density function (PDF) of RVsX1andX2, respectively. Based on Ref.[8], they can be given by
(18)
(19)
(20)
Substituting Eqs. (18) and (19) into Eq. (16) yields
(21)
Substituting Eqs.(18), (19) and (20) into Eq.(17) yields
(22)
where
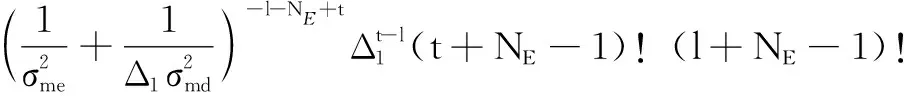
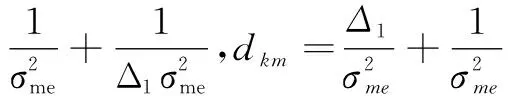
We assume that each SD has the same weighting coefficient. Hence, the IP of the investigated system relying onSmcan be defined as
(23)
As previously mentioned, each SD pair can be selected to transmit with equal opportunity in the RSDS scheme. Moreover, relying on the law of total probability[13], the IP of the multiple SD pairs in the RSDS scheme can be given by
(24)
2.2 Proposed TAS-OSDS scheme
This subsection presents the IP analysis of the TAS-OSDS scheme. As shown in Eq.(10), the index of the chosen SD pair is denoted byoin the scheme. Hence, with the aid of the TAS-OSDS scheme, the IP of the signal transmitted bySoandSkcan be formulated as
(25)
and
(26)
Using Eqs.(6) to (9), Eqs.(25) and (26) can be rewritten as
(27)
and
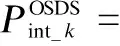
(28)
respectively, whereΛ1=Pt/Ps. Based on Eq.(11), we can obtain
(29)
(30)
(31)
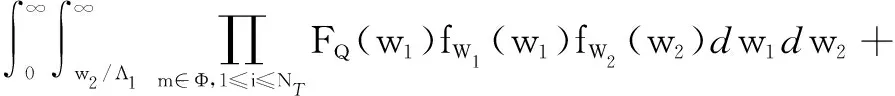
(32)
Based on Ref.[10],FQ(w),fW1(w1) andfW2(w2) can be given as
(33)
(34)
(35)
Using Ref.[11] and substituting Eqs. (33) and (34) into Eq.(31) yields
(36)
Using Eqs.(33), (34) and (35), Eq.(32) can be obtained as
(37)
Then, with the aid of the definition in Eq.(23), the IP of the multiple SD pairs aided by the proposed TAS-OSDS scheme can be given by
(38)
From Eq.(38), we can not only evaluate the PLS of wireless transmissions, but also investigate the effects of the channel gain, the number of antennas, and the number of source-destination (SD) pairs on the attainable PLS level of wireless transmissions.
3 Numerical Results
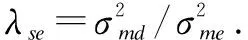
(39)
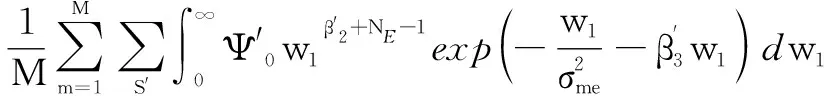
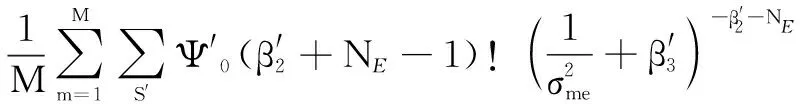
(40)
Fig.2 shows the IP vs. MER of the traditional RSDS, non-coop as well as of the proposed TAS-OSDS schemes for different (NT,NR,NE) by plotting Eq.(24), Eq.(40) and Eq.(38), as a function of the MER. It is shown in Fig.2 that as the number of antennas (NT,NR,NE) increases from (NT,NR,NE)=(1,1,1) to (2,2,2), the IP of the RSDS, non-coop and TAS-OSDS schemes will be reduced correspondingly, which confirms that the PLS of wireless transmissions can be enhanced by increasing the number of antennas of the SD pairs. Moreover, Fig.2 also shows that although the IP of all schemes will be decreased as the MER increases from -10 to 15 dB, the proposed TAS-OSDS schemes can still achieve the lowest IP among the RSDS, non-coop, and TAS-OSDS schemes. Hence, at a given IP constraint, the proposed TAS-OSDS scheme can be used to guarantee the PLS of wireless transmission in a lower MER case.
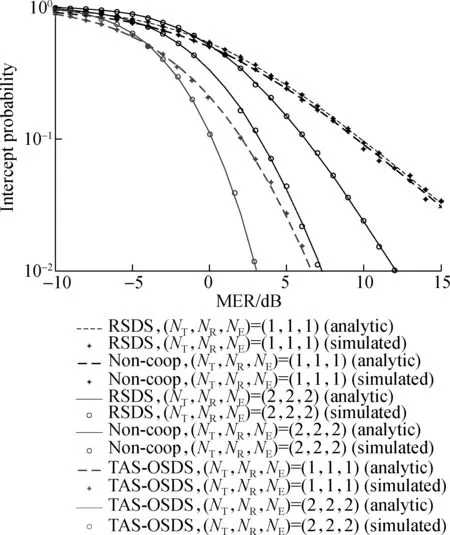
Fig.2 Comparison of intercept probabilities under different MERs
Fig.3 illustrates the IP vs. the number of source-destination pairsMof the traditional RSDS, non-coop and the TAS-OSDS schemes for different numbers of antennas ofE. As shown in Fig.3, increasing the number of antennas ofEwill increase the risk of the wireless transmission being eavesdropped upon successfully in the traditional RSDS, non-coop and the TAS-OSDS schemes, whereas the IP of the TAS-OSDS is lower than that of both the RSDS and non-coop schemes. Furthermore, it can be seen from Fig.3 that although the PLS of wireless transmissions will be degraded, the IP of wireless transmissions will be significantly decreased relying on increasing the number of SD pairs in the proposed scheme, demonstrating the superiority of the proposed TAS-OSDS scheme. This is due to the fact that the cooperation between SD pairs will be more beneficial for increasing the PLS of wireless transmissions in the proposed TAS-OSDS scheme, whereas no benefit can be achieved in either the RSDS or non-coop schemes.
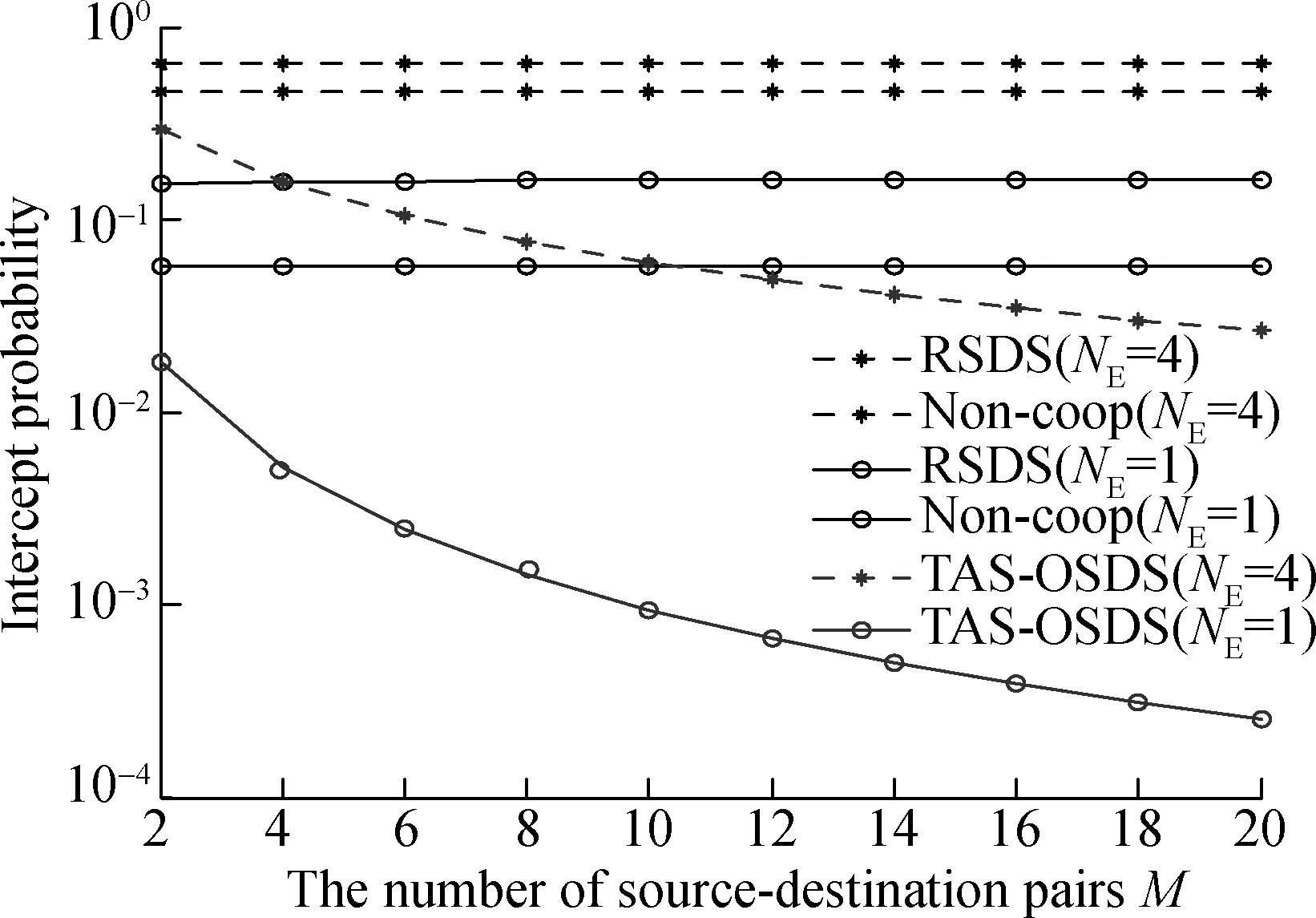
Fig.3 Intercept probability with respect to the number of SD pairs M
4 Conclusion
1) In this paper, we study PLS for a heterogeneous wireless network including multiple SD pairs in the presence of an eavesdropper, where the SD pairs access the shared spectrum in a dynamic manner.
2) We explore a cooperation framework for SD pairs to protect against eavesdropping attacks. Specifically, an SD pair is chosen as the transmitting pair at the beginning of the given transmission slot, then it participates in collaborative transmitting among the SD pairs. Moreover, the IPs of the proposed TAS-OSDS as well as the conventional RSDS schemes are analyzed for comparison purposes.
3) It is shown that the TAS-OSDS scheme achieves a better IP performance than that of the RSDS and conventional non-cooperation schemes, where each source communicates with its corresponding destination without co-operating with other SD pairs in the non-cooperation scheme. Furthermore, with an increasing number of the SD pairs, the IP of the TAS-OSDS scheme will be reduced clearly.
 Journal of Southeast University(English Edition)
2019年3期
Journal of Southeast University(English Edition)
2019年3期
- Journal of Southeast University(English Edition)的其它文章
- Experimental investigation of oil particles filtration on carbon nanotubes composite filter
- Projection pursuit model of vehicle emission on air pollution at intersections based on the improved bat algorithm
- Effect of waste concrete with different strengthon mechanical properties of recycled fine aggregate mortar
- Tensile behaviors of ecological high ductility cementitious composites exposed to interactive freeze-thaw-carbonation and single carbonation
- Travel time prediction model of freewaybased on gradient boosting decision tree
- Image denoising method with tree-structured group sparse modeling of wavelet coefficients
