Application Analysis of ACL Technology in Small and Medium Sized Network Security Management
Jiang Junhua
(Yixing Higher Vocational and Technical School,Wuxi,Jiangsu 214200)
Abstract:The progress of computer hardware and software technology has promoted the rapid development of network technology,and attacks on the Internet are increasing.In order to ensure network security,network administrators must ensure the security of data and resources by restricting users'permissions while opening enough network permissions.In view of this situation,although network administrators can use a lot of security technology means,due to the limitations of various aspects of the small and medium-sized network conditions,we can only switch to the idea of using access control list(ACL)instead of expensive hardware firewalls to achieve the control and filtering of network data flow.In addition,the simple configuration of ACL can also realize the filtering of some common viruses,and finally achieve the basic and low-cost network security goal.
Keywords:network security;ACL;router;interchanger;virus filter
In recent years,with the rapid development of computer hardware and software technology,network technology has also developed rapidly,and attacks on the Internet are increasing.How to guarantee network security has become one of the problems that seriously trouble the network administrators of small and medium-sized network.Because of the demand of consolidating and expanding the business,the network administrator must open enough permissions to allow users access to network resources;in addition,network administrators must ensure the security of data and resources by strictly restricting users'rights.In the face of various kinds of network attacks,although network management can use a lot of network security technology,but due to the limitations of conditions,small and mediumsized network can use limited funds.We can switch to the idea of considering the use of access control list(ACL)to replace the expensive hardware firewall to achieve the control and filtering of network data flow,and finally achieve the basic and cost controllable network security goals.
I.Summarize of ACL
(i) ACL Technology
Access control lists is called ACL,it is a network security technology based on packet filtering mechanism,which filters packets passing through the interface according to pre-set conditions to de-termine whether it is allowed to pass.ACL can can be widely used on the router or layer 3 switches,by reading the information in the third and fourth layers such as the source address,destination address,source port,destination port,etc.,and combining with the preset conditions to allow or deny specific packets in and out of the network so as to achieve the control of network access,thus ensuring the safe operation of the network effectively.Users can tailor a series of access rules based on specific information in the packet.Each rule describes the corresponding action to be taken for a packet that matches specific information:Allow or deny passage,and then apply these user-preset rules to the entry or exit directions of the corresponding port,so that the data flows in a particular direction on particular ports must be in and out the routers or switches according to the specified ACL rules.By using ACL technology,network administrators can achieve the purpose of restricting the illegal network activities of a specific IP address or a certain network segment of PC[1].
(ii) Classification of ACL
ACL can be divided into many kinds,and the most commonly used ones are mainly two categories.
1.Standard ACL
The standard ACL is the simplest,it filters only by using the source IP address in the IP packet,the table number range is 1-99 or 1300-1999.
The grammatical structure of standard ACL statements:
router_config#ip access-list standard name
router_config_std_nacl#permit/deny 172.16.1.0 255.255.255.0
2.Extended ACL
Extended ACL provides more matches than standard ACL,so it has more refined and powerful functionality,and can filter for source address,destination addresses,source ports,destination ports,TCP connections,protocol types,etc.,the table number range is 100-199 or 2000-2699.
The grammatical structure of extended ACL statements:
router_config#ip access-list extended name
router_config_ext_nacl#permit/deny tcp 172.16.1.0 255.255.255.0 2.2.2.2 255.255.255.255 eq port
While using access control lists,pay special attention to the following points:1.The“1”in wildcard mask means to ignore the corresponding bits in the IP address,and“0”means that the bits must match.The two special wildcard masks are'255.255.255.255'and'0.0.0.0',the former represents the keyword“any”,and the later represents the keyword“host”.2.Inbound and outbound interfaces.When an access control list is applied to the corresponding interface,the user must indicate whether the access control list is applied to the data inflow or outflow direction.3.Whenever possible,consider placing the extended ACL close to the filter source so that the filter rules created do not adversely affect the normal data flow on other interfaces;put the standard ACI close to the destination,because the standard access control lists can only use the source address,and if move it close to the filter source,legitimate packets will be prevented from flowing to other ports.4.After the ACL is opened,whether configured or not,an implicit'deny'will negate all addresses,so there must be at least one'permit'statement in the ACL[2].
II.Application Case Study of ACL Technology in Small and Medium-Sized Networks
The application of ACL technology is widely used.We take the topology of a small and mediumsized network(router:Digital China DCR-2655)as an example to briefly analyze the basic application configuration of ACL on this basis.
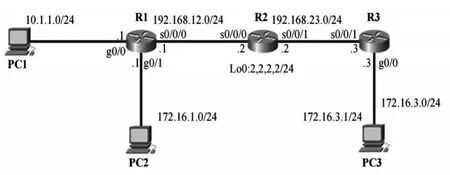
1.Request for denying PC2 segment access to router R2.Create a standard ACL configuration that meets the requirements:
R2_config#ip access-list standard P2ToR2
R2_config_std_nacl#deny 172.16.1.0 255.255.255.0
…
2.Request for only allowing hosts in the PC2 segment to access router R2's WWW service.Through analysis,create an extended ACL configuration that meets the requirements.
R1_config#ip access-list extended P2ToR2
R1_config_ext_nacl#permit tcp 172.16.1.0 255.255.255.0 2.2.2.2
…
3.Only allow hosts in the PC3 to access router R2's WWW service from 8:00 to 18:00 each day.Create time-based access control list configuration:
R3_config#time-range P3ToR2
R3_config_time_range#periodic daily 8:00 to 18:00
…
III.Application Analysis of ACL Technology in Antivirus
At one time,virus such as Blaster,Sasser have brought a heavy blow to the entire Internet.So far,the Internet we use still has a large number of viruses and their variants every day,they are everywhere,looking to harm the security of the network.Therefore,when configuring network devices such as routers or switches,network administrators can consider filtering these viruses through simple configuration of ACL(access control list)to keep them out and ensure the stable operation of the network.By querying relevant public information,we can obtain the commonly used network port numbers–Blaster virus and its variants:corresponding TCP port number 135,139,445 and 593,UDP port number 69,135,137 and 138;shell programs involving remote command:corresponding TCP port numbers 4444,135,139,445,4444,UDP port number 69,135,137 and 138.Sasser virus and its variants:corresponding TCP port 5554,445,9996.SQL worm virus:corresponding TCP port number 1433,UDP port number 1434[3].
ACL filters configuration for specific viruses:
switch(config)#ip access-list extended acl
switch(Config-IP-Ext-Nacl-acl)#deny tcp host-source 192.168.1.1 s-port
445 any-destination
…
IV.Conclusion
In general,if ACL technology can be properly used,it will become a powerful filtering tool in the hands of network administrators.In addition to filtering the traffic through the network,it can also further improve the security of the network by preventing and controlling virus attacks and restricting Internet access.But like a double-edged sword,poorly designed access control list configurations can backfire,placing a heavy additional burden on routers and switches and,in the worst cases,causing the entire network to go down.Therefore,only by properly planning and configuring ACL can we give full play to its ability to efficiently manage small and medium-sized networks.
- 中阿科技論壇(中英文)的其它文章
- Application of Statistical Technique in the Management of Power Supply Enterprises at County Level
- Analysis of Existing Problems and Countermeasures of Enterprise Performance Management
- Construction Analysis of Urban Underground Comprehensive Pipe Corridor Structure
- Evaluation of Uncertainty in Determination of Sucralose Content in Edible Betel Nut by High Performance Liquid Chromatography
- Main Disease and Control Method for Highway Widening Roadbed
- Application of Reverse Osmosis Technology in Boiler Water Treatment of Power Station

